In the modern digital world, “Token” is no longer an unfamiliar term to many internet users. In many cases, token acquisition plays an important role in user authentication and authorization. In this article, we will explore “What is Get Token?” and how to get a token with full powers.
What is Get Token?
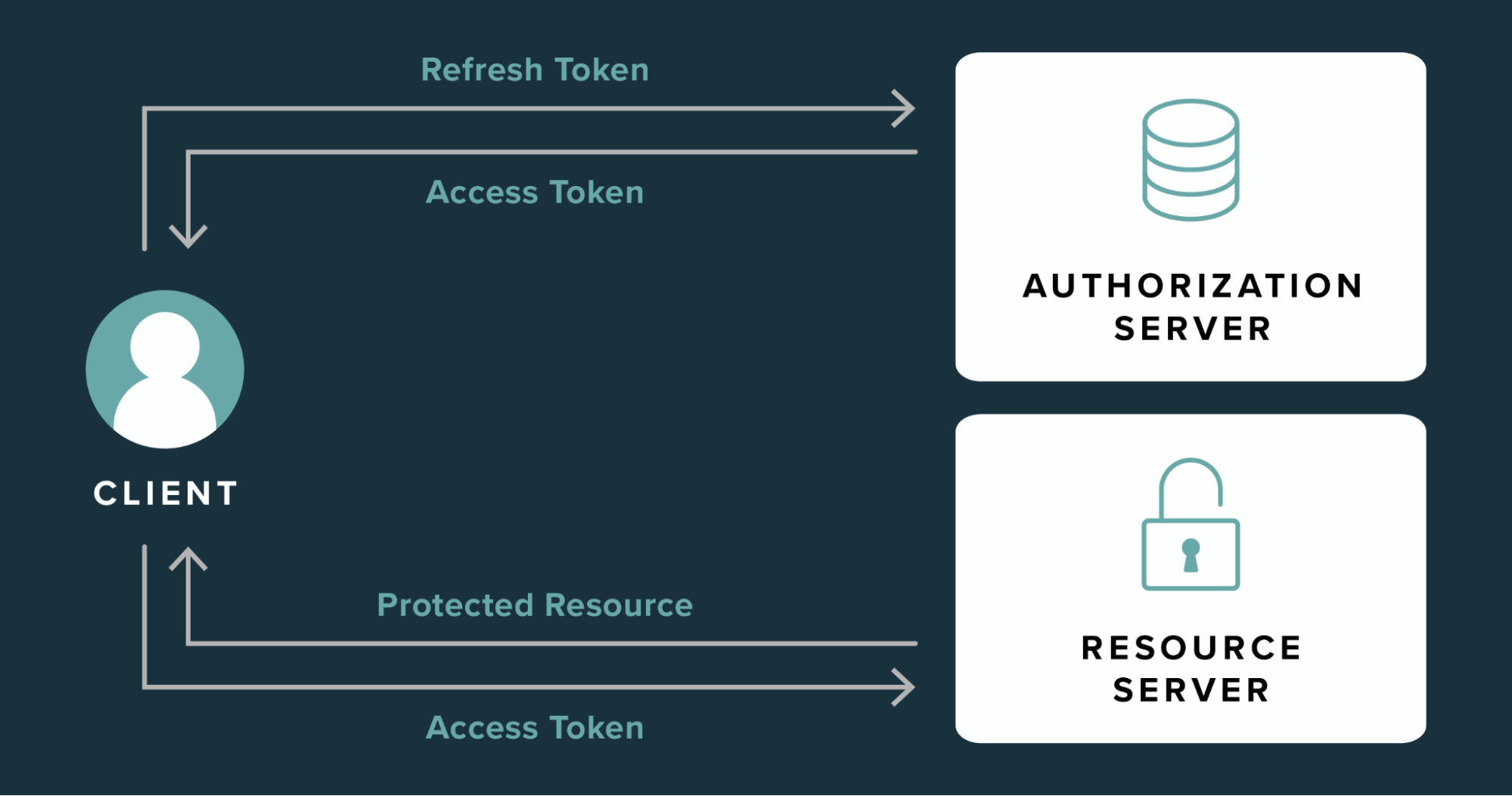
Get Token is the act of obtaining an Access Token – a random string of characters given to the application or user by Facebook after they log in successfully. This token is not simply a token of authentication, but also a key to many features and services that applications or users can take advantage of.
In today’s complex digital environment, Access Tokens play an important role in authentication and authorization. When an application or user requests an Access Token from Facebook, they are actually requesting a license or “token” from the world’s largest social network.
Access Token allows applications or users to access some information and perform some actions on Facebook accounts without having to log in again. With the granted permissions, users can perform tasks such as posting, reading messages, uploading photos, or even managing pages and groups of which they are admins.

Some popular types of Tokens today
Currently, there are several popular tokens used in applications and systems around the world. Here are some popular token types:
JSON Web Token (JWT)
JWT is a widely used open standard for securely transmitting information between parties in the form of a JSON string. JWT is commonly used for authentication and authorization, and it can be encrypted to ensure data integrity.
OAuth Access Token
OAuth Access Token is a type of token issued after the user authenticates through OAuth. This get Token is used to authorize access to resources and services that the user has authorized, without having to provide a username and password again.
Refresh Token
Refresh Token is often used in the OAuth authentication process to refresh or update the Get Token without having to ask the user to log in again. Refresh Token has a longer lifespan, helping to maintain system security.
Session Token
Session Token is a type of token used to maintain a user session on an application or website. This token is typically generated when a user logs in and is used to identify the user for the duration of the session.
ID Token
ID Token is a type of token used in the OIDC (OpenID Connect) authentication process to provide authentic information about users. ID Token usually contains information such as the user’s ID, authentication information, and other secondary information.
The simplest way to Get Token with full rights
The simplest way to get full rights tokens is through the use of Facebook Business tools and interfaces. Below are specific instructions:
Method 1: Get tokens via Facebook Business
This method is currently the most commonly used, but may require you to perform two-factor authentication (2FA) via an app or SMS code. By following these two simple steps, you can collect full authority tokens:
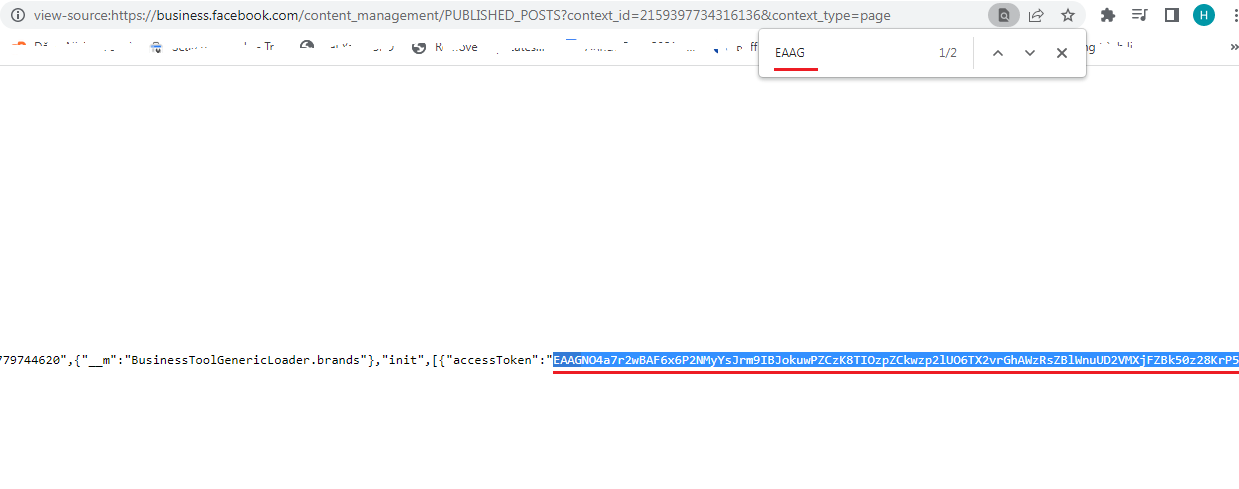
- Access to https://business.facebook.com/contentmanagement.
- Press Ctrl + U to open the page source code, then press Ctrl + F and find the string containing EAAG (open the image below in a new tab to see clearly):
After finding the necessary string, copy the highlighted text. That is the token you need to collect.
Method 2: Get Facebook tokens through the Instagram application
Here is a safe method of getting tokens, with almost full authority for you:
- First, log in to the Facebook account you want to get tokens for.
- Next, tap to accept permissions for the Instagram app.
- Copy the link in the box below and paste it into your browser’s address bar to access.
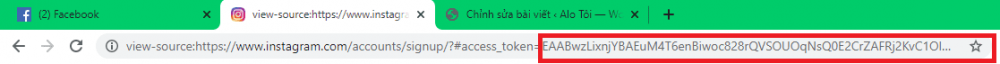
Copy the following code:
view-source:https://www.facebook.com/dialog/oauth?client_id=124024574287414&redirect_uri=https://www.instagram.com/accounts/signup/&&scope=email&response_type=token
Here, you will see the Facebook token you need to get in the address bar of your web browser.
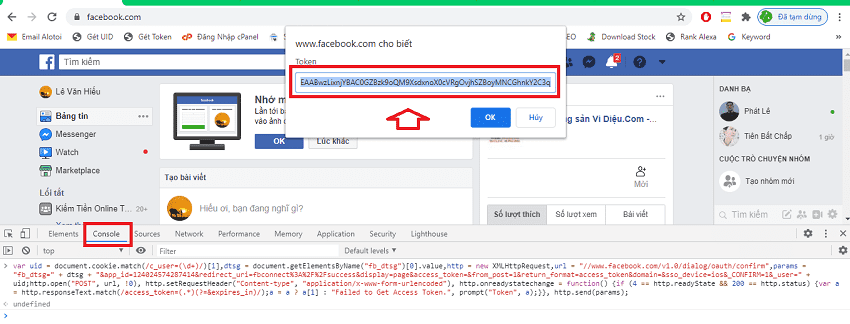
Method 3: Get Facebook token using Code F12
Click here and copy the code inside.
- Visit the Facebook page and then press the F12 key or Ctrl + Shift + C to open the Console window.
- Paste the code you just copied into the Console window. At this point, you will see the Facebook account token.
Note: If you don’t get the token, consider authorizing Instagram using method 1.
Method 4: Get Facebook tokens through the View Source page
Although the tokens obtained through this method may not have full rights, if you only need to use them for basic purposes such as liking, commenting, posting, etc., you can get the tokens accordingly. following way:
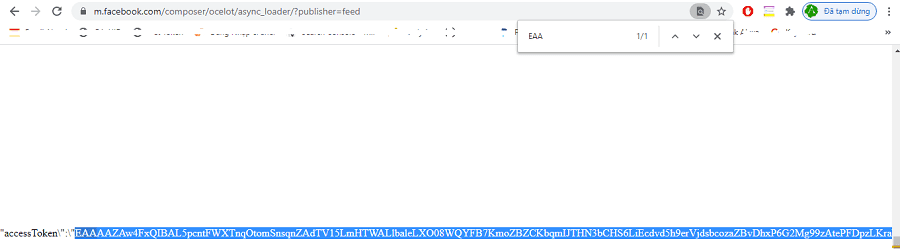
- Visit to get tokens.
- Press the key combination Ctrl + U to view the source code of the page.
- Use the key combination Ctrl + F and enter “EAA” to search for tokens.
Please copy the highlighted code as shown in the image to use. That is the token you need to collect.
Some notes when performing Get Token with full rights
When obtaining full rights tokens, there are a few important things to keep in mind to ensure the security and efficiency of the process. Here are some important notes:
Information security
Do not share tokens: Full permission tokens provide full access to Facebook accounts. Please keep this token private and do not share it with anyone unnecessarily.
Handle tokens securely: Always store and handle tokens securely. Avoid storing tokens in insecure storage areas or transmitting token data over insecure channels.
Trusted authentication
Use trustworthy sources: Always use trustworthy sources to obtain tokens, such as the official Facebook Business page.
Check the URL: Before providing login information or giving app access, check the URL to make sure you’re on Facebook’s official website.
Check access permissions
Check access permissions: Before providing access to an app, carefully review the permissions the app requests and only grant what you need.
Collect necessary tokens: Only collect tokens necessary to perform the specific job you want to complete, avoiding collecting too much unnecessary access.
Follow and update
Monitor and update tokens: Monitor and update tokens periodically to ensure their safety and effectiveness.
Destroy unnecessary tokens: If not needed, destroy unnecessary or expired tokens to avoid security risks.
Get Token is an important process in authenticating and authorizing users in applications and systems. Through this article by Proxyv4.net, us you have a better understanding of what it means to get tokens and how this process is carried out. Follow us for more useful information every day!